“Every month, when we release the new episode,
“Information Security” becomes the buzz in the office.
I have never seen such a thing. When did information
security training become something our employees talk
about? When we introduced NINJIO!”


“Previous products were very long and boring. Staff
would never take the time to watch the entire training
and it was difficult to keep their interest and attention.
From the start, NINJIO was well received and got the job
done without wasting valuable time.”

“Long gone are the days of lengthy videos that are
ineffective, and boring to users. NINJIO videos are
short, relevant, and frequent. Each video is 3-4
minutes long and will focus on telling a story of
a real breach, and then give users a simple piece
of advice to follow.”

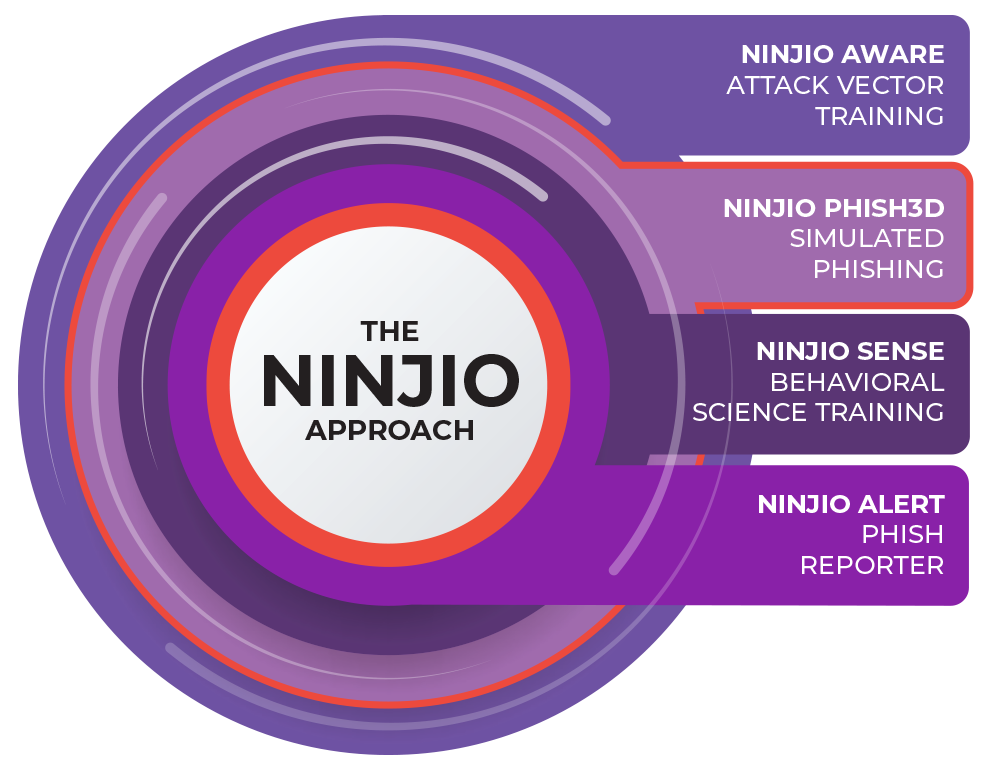
 Attack vector-based phish testing
Attack vector-based phish testing Emotional susceptibility testing
Emotional susceptibility testing Automated difficulty levels
Automated difficulty levels